The encryption process is an essential element of data security in the modern age and serves as a safeguard that shields sensitive information from the scrutiny of others. It is available in two principal types such as encrypted with symmetric keys and private key encryption.
Understanding the distinctions between Symmetric Key Encryption and Public Key Encryption options is essential for protecting data in a variety of settings. The intricacies of public and symmetric key encryption and will highlight their features, uses and advantages, as well as disadvantages and key differences.
It will help you make an informed choice regarding which encryption method is best suited to your security needs.
What is Symmetric Key Encryption?
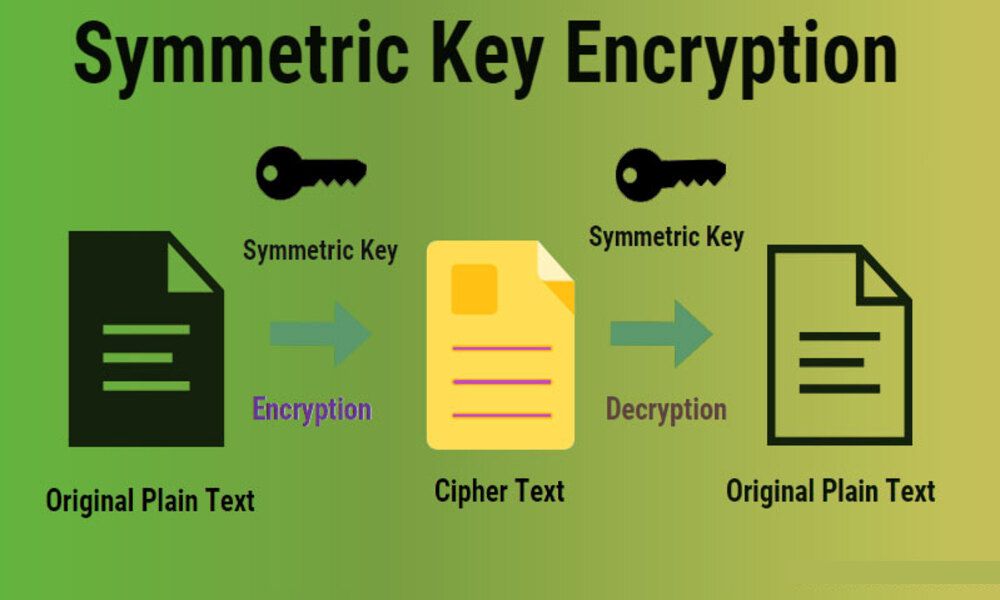
Symmetric key encryption (also referred to as secret key or conventional encryption) is a cryptographic technique that employs one shared secret key for both encryption and decryption purposes. With this approach, both sender and recipient use the same secret key to safeguard the confidentiality and integrity of their transmitted information.
Here’s how symmetric key encryption works:
Key Generation: Synchronous key encryption algorithms require the generation of a secret key; typically this comprises an encrypted string of bits or characters that should remain secret between communicating parties.
Encryption Process: To encrypt data, the sender applies a secret key and encryption algorithm to their original message (plaintext). This transforms it into encrypted ciphertext that has now been sent onward.
Decryption Process: After receiving the ciphertext, its recipient applies their secret key and decryption algorithm to reverse its encryption and convert it back into plaintext. This reverses any potential leakages of information contained within.
Key Management: Due to using the same secret key for both encryption and decryption, secure key management is absolutely critical. The secret must be shared securely between sender and recipient without interception by third parties.
Symmetric key encryption offers numerous advantages, including speed and efficiency in encryption/decryption processes, ease of implementation, and suitability for encrypting large volumes of data. However, it also poses certain challenges, including key distribution and management; these become even more apparent as more parties communicate.
What is Public Key Encryption?
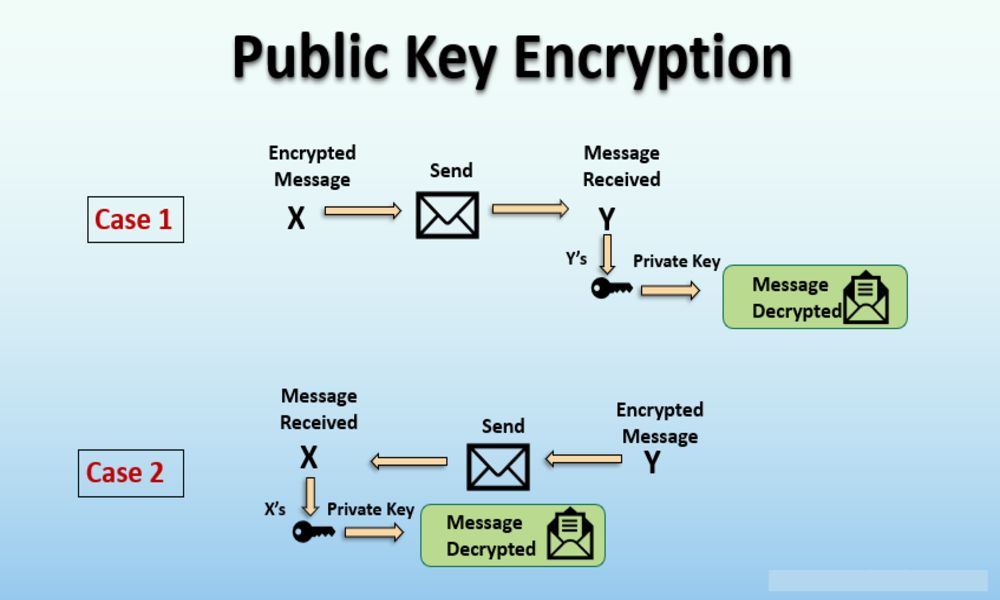
Public key encryption (sometimes referred to as asymmetric encryption) is a cryptographic technique that uses two mathematically related keys for encryption and decryption: public key and private key. As opposed to traditional symmetric key techniques which utilize just one key for both operations, public key encryption employs two separate keys for these operations.
Here is how public key encryption works:
Key Generation: Each user generates two keys – known as public and private keys – which they freely share with others while their private key remains private and only known to themselves.
Encryption Process: To secure their message, individuals need to use their recipient’s public key as part of an encryption process that converts plaintext to ciphertext.
Decryption Process: The recipient – who owns their respective private key – uses this key to decrypt ciphertext and restore the original plaintext.
Key Properties: Each key pair in public key encryption possesses unique properties. A public key may be freely distributed and used by anyone for encryption; however, only its matching private key can decrypt it – something the former cannot do. Public key encryption provides numerous advantages over its symmetric counterpart, including greater security and key management benefits. Some of these advantages include:
Key Distribution: With public key encryption, no secure key distribution is necessary; public keys may be freely shared and used by any individual – making setting up secure communication channels easier than ever before.
Confidentiality and Authentication: Public key encryption provides secure transmission of confidential data as only those possessing its corresponding private key are capable of decrypting it. Furthermore, digital signatures made from private keys allow for the authentication of sender’s identity.
Secure Communications Channels: Public key encryption can be used to establish secure communication channels such as secure socket layer (SSL) or transport layer security (TLS), which are widely utilized to protect sensitive information during online transactions and conversations over the internet.
Public key encryption may be slower and computationally more expensive than its symmetric key counterpart due to the complex mathematical operations involved. Therefore, hybrid encryption provides the ideal compromise by employing both approaches simultaneously.
Comparison Table of Symmetric Key Encryption and Public Key Encryption
Here’s a comparison table outlining the key differences between symmetric key encryption and public key encryption:
| Criteria | Symmetric Key Encryption | Public Key Encryption |
|---|---|---|
| Key Types | Single shared secret key | Mathematically related key pair (public key and private key) |
| Key Distribution | Challenging – requires secure key exchange | Simple – public keys can be freely shared |
| Encryption Speed | Fast and efficient | Slower compared to symmetric encryption |
| Decryption Speed | Fast and efficient | Slower compared to symmetric encryption |
| Key Management | Complex key distribution and secure storage required | Private key must be kept secret, public key can be shared |
| Security Strength | Relies on the secrecy of the shared key | Relies on the computational difficulty of key pair |
| Applications | Encrypting large amounts of data | Secure communication, digital signatures, key exchange |
| Scalability | Not suitable for large-scale communication | Suitable for large-scale communication |
| Hybrid Encryption Compatibility | Can be used as a component in hybrid encryption | Can be used as a component in hybrid encryption |
Note: The comparison table provides a general overview and highlights the main differences between symmetric key encryption and public key encryption.
It’s important to consider specific use cases and security requirements when choosing the appropriate encryption method.
Fast and efficient encryption and decryption processes
Symmetric key encryption stands out as an efficient and fast method of encryption and decryption processes, with fast encryption/decryption processes being its hallmarks.
Here is why it is considered so:
Single Key Operation: With symmetric key encryption, the same key is used both for encryption and decryption – meaning straightforward operations using just one key, leading to lower computational overhead and faster encryption and decryption speeds.
Streamlined Algorithms: Symmetric key encryption Algorithms such as Advanced Encryption Standard (AES) and Data Encryption Standard (DES), have been Optimized to be highly efficient and fast in Execution on various computing Platforms, including hardware Acceleration. They have undergone extensive research to ensure efficient use on these platforms.
Simplicity of Operations: Symmetric key encryption algorithms utilize simple yet efficient mathematical operations, including bit-level XOR and substitution-permutation networks, that can easily be implemented both hardware and software to facilitate quicker encryption/decryption processes.
Symmetric Key Encryption Is Ideal for Bulk Data Encryption: Symmetric key encryption is Particularly well-suited to protecting large Volumes of data, due to the single key used in its encryption and decryption Processes, making them suitable for processing bulk information without incurring significant computational overhead.
This makes symmetric key encryption ideal in situations that demand fast encryption or decryption processes such as protecting storage or network transmissions.Notably, the speed and efficiency of symmetric key encryption may differ depending on its specific algorithm, key size, hardware capabilities and implementation details.Although symmetric key encryption excels at speed, it may present challenges in key distribution and management – especially where multiple parties are involved.
Advantages of symmetric key encryption
Symmetric key encryption offers several advantages that have made it a widely-utilized encryption method.
Here are a few key benefits of symmetric key encryption:
Speed and Efficiency: Symmetric key encryption algorithms are specifically designed to be fast and efficient, making them suitable for quickly encrypting and decrypting large volumes of data quickly.Since only one key needs to be used for both encryption and decryption purposes, computational overhead remains relatively low for these methods, leading to faster processing times than with other encryption techniques.
Simplicity and Implementation: Symmetric key encryption algorithms tend to be easier and quicker to implement compared to public key algorithms, with simple operations like XOR and substitution-permutation networks used as core operations involved in their implementation.This simplicity facilitates efficient implementation across both software and hardware systems.
Resource Efficiency: Symmetric key encryption requires less computational resources such as processing power and memory than public key encryption, making it more suitable for resource-constrained devices such as embedded systems or Internet of Things devices where computational efficiency is key.
Compatible with Bulk Data Encryption: Symmetric key encryption is well-suited to protecting large volumes or streams of data at once.
With efficient encryption and decryption processes that ensure secure transmission or storage of bulk information quickly and reliably, symmetric key encryption makes an excellent solution for data-intensive applications.
Secure Communication in Closed Systems: Symmetric key encryption can provide secure communication within closed systems when there exists a predetermined and trusted relationship among communicating parties.As the shared secret key can only be known to authorized entities, this form of cryptography ensures maximum confidentiality and integrity for exchanged information.
Integration into Hybrid Encryption Systems: Symmetric key encryption is often included as part of hybrid encryption systems.
Hybrid encryption combines the best aspects of both symmetric and public key encryption, capitalizing on their respective strengths to achieve effective data encryption utilizing bulk data encoding using symmetric key encryption, while public key encryption provides for key exchange and management security.
While symmetric key encryption offers certain benefits, it also presents challenges in terms of key distribution and secure key management when communicating between multiple parties. Therefore, when choosing an encryption method it is important to carefully consider individual requirements as well as limitations when making this decision.
Limitations of symmetric key encryption
Although symmetric key encryption provides many benefits, it also has some downsides which should be taken into account.
Below are some key disadvantages of using this method of protection:
Key Distribution: One of the primary difficulties of symmetric key encryption lies in securely disseminating its shared secret key to all intended recipients. As it serves both encryption and decryption functions, keeping its use confidential requires safeguarding it against unauthorized access; creating an effective key distribution mechanism becomes even more challenging and vulnerable when multiple parties are involved.
Key Management: Symmetric key encryption requires vigilant key management practices in order to maintain the security and integrity of its shared secret key, from generation, storage, distribution and changeover. Furthermore, as communication parties multiply so too does complexity of key management. Updating and changing keys regularly becomes increasingly challenging within large systems.
Lack of Forward Secrecy: In symmetric key encryption, once the shared secret key has been compromised it becomes possible to decrypt past and future encrypted data, leaving your previously encrypted information exposed and vulnerable. As such it highlights the necessity of secure key management practices as well as periodic key rotation to reduce risks.
Scalability and Key Proliferation: Symmetric key encryption becomes less scalable as more parties communicate securely; in a situation with multiple users communicating, each pair of users requires their own secret key for communication purposes; with each additional user comes more keys that require management overheads that multiply exponentially.
Limited Authentication and Non-Repudiation: Symmetric key encryption does not inherently offer secure authentication and non-repudiation mechanisms. While it ensures confidentiality and integrity of data, it does not verify or prevent deniability by sender; additional mechanisms, such as digital signatures are often needed to provide sufficient authentication and non-repudiation mechanisms.
Key Exchange in Unknown Environments: If exchanging keys securely is difficult in untrusted networks or with unfamiliar parties, symmetric key encryption alone may not suffice – creating an encrypted communication channel between parties to exchange the shared secret key becomes essential.
To overcome some of these limitations, hybrid encryption techniques are increasingly being employed, combining the strengths of both symmetric key encryption and public key encryption for improved key management, scalability, and security.
Conclusion
Symmetric key encryption and public key encryption are two fundamental methods with distinct characteristics and uses. Symmetric key encryption offers fast and efficient encryption/decryption processes, making it suitable for protecting large amounts of data efficiently.However, its use requires one shared secret key that poses unique distribution/management challenges.
Public key encryption provides secure communication, digital signatures and key exchange capabilities using mathematically related key pairs containing public keys for encryption and private keys for decryption. While public key encryption provides easy key distribution it tends to be slower.
Factors to consider when choosing encryption methods
When selecting an encryption method, several factors should be taken into account to make the optimal choice for the particular use case and security needs of an organization.
Here are a few essential ones:
Security Strength: Evaluate the level of protection offered by an encryption method by taking into account factors like its strength, key size, resistance to attacks and any known vulnerabilities. Assess whether this encryption method provides adequate protection for sensitive data that requires protection.
Performance and Efficiency: Carefully consider the computational overhead and performance impact of any encryption method you consider using, along with speed of encryption/decryption processes, resource utilization (CPU, memory) utilization, efficiency of algorithm implementation. Evaluate whether this encryption method can accommodate expected workload without significant delays or resource limitations.
Key Management: Assess the key management requirements of an encryption method and consider factors such as distribution, generation, storage and rotation when making decisions on which keys should be managed and distributed securely across multiple parties or when frequent key changes are necessary. Evaluate any complexities or feasibility associated with successfully doing so when more than one party are involved or frequent changes need to occur.
Scalability: Evaluate the scalability of an encryption method. Determine whether it can efficiently support large-scale deployments with multiple users or devices and assess its impact on key management, computational resources and performance as the system scales up.
Compatibility and Interoperability: Evaluate whether the encryption method you have selected can integrate well with existing systems, protocols, standards and technologies; test its integration with other security mechanisms or encryption technologies; ensure it can function seamlessly with required communication channels, platforms or applications;
Compliance Requirements: Regulatory compliance can impact your choice of encryption method. Certain industries or jurisdictions may have specific encryption standards or guidelines to follow in order to meet legal and regulatory compliance.
Usability and User Experience: Take into account the implications for user usability and experience when selecting an encryption method, taking into account factors like ease of implementation, end user comfort levels, availability of user-friendly tools or libraries and compatibility with desired user interface or workflow requirements.
Key Exchange and Trust: Assess the trust assumptions and key exchange mechanisms required by your encryption method. Consider whether secure key exchange is feasible and practical when communicating with unknown or untrustworthy parties, and assess if authentication, non-repudiation, or verification mechanisms exist for participants in communication sessions.
By carefully considering these factors, organizations and individuals can make educated choices when selecting an encryption method best suited for their particular requirements, protecting confidentiality, integrity, and security of sensitive data.